After finishing the integration of Jenkins with LDAP, this post shows how to create permission roles based on user groups (memberOf). As I said in the previous post, I created 2 groups and 2 users, to exemplify how this management works.
Preparation.
Now, we need to install and enable another plugin, so in Manage Jenkins > Plugins, install the “Role-based Authorization Strategy” plugin.

Once enabled, you may need to restart Jenkins
The next step is to go to Manage Jenkins, Security and in the Authorization configuration in the Authentication section, change the value to “Role-Base Strategy”.
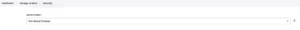
Now, in Manage Jenkins, in the Security group, a new item should appear, “Manage and Assign Roles“.
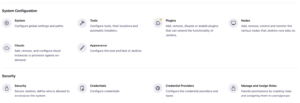
Roles.
In “Manage Jenkins”, select the option “Manage and Assign Roles“, and a screen like below will be displayed.
I won’t go into detail about each option, the plugin page is very well detailed. I will only show how to create Roles and groups to control LDAP user permissions.
The first step is to create a Global Role with fewer permissions than an admin, I created, as you can see, “PipelineReadOnly“, with only read permissions at some points.
Later on, when we integrate GitLab with Jenkins or Consul, we will have new roles. But that’s for later.

Groups.
In the menu on the left, under Assign Roles, we will actually create the groups that will be associated with LDAP.
Groups are not loaded automatically, we need to register all of them that we will use, and they must have the same name (CN) as the group. When recognised with the same name as a group (in the previous post there is the query for this listing – Group search base) the group icon next to it is displayed.
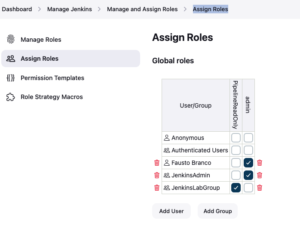
With the groups registered and recognised, it is then possible to assign them to the previously created role. In the example above, I assign the JenkinsAdmin group to the admin role and the JenkinsLabGroup group to the PipelineReadOnly role.
When saving, it is possible to do a test with the user usr-service-jenkins who is a memberOf of JenkinsLabGroup. When logging in, you will notice that there are few permissions, unlike the user who is a memberOf of JenkinsAdmin.
Leave a Reply