Preparation.
In this post, I will show you how to configure Jenkins integration with LDAP and assign permissions. In Jenkins the configuration is a little different, as it is more complete, with more filter possibilities.
Also, Jenkins uses Java, so the certificate for LDAP/TLS communication needs to be in a Keystore/Truststore.
Jenkins does not natively have this integration, so we will use two plugins, the “LDAP Plugin”, for integration with LDAP and the “Role-based Authorization Strategy” for managing permissions per LDAP group.
Attention, when completing this configuration, Jenkins will only accept LDAP authentications. There is a plugin to enable Mixing Authentications, but it has not been updated for some time: Mixing Security Realm.
In another post, I will show how to roll back this modification if you lose your administrative accounts or connection with LDAP.
LDAP Plugin.
So, to be able to integrate Jenkins with the LDAP that was created, we need to add the “LDAP Plugin” plugin for this.
Open your Jenkins with an administrative account, click on Manage Jenkins, choose the Plugins item.
If you already have it installed, click on Installed plugins and in the search bar, search for LDAP.
If it is not yet installed, under Available Plugins, proceed with the installation. This plugin is part of the suggested installation package at the beginning of the Jenkins installation.
Enable the plugin. If the plugin is not yet enabled, then you will need to restart Jenkins for it to take effect.

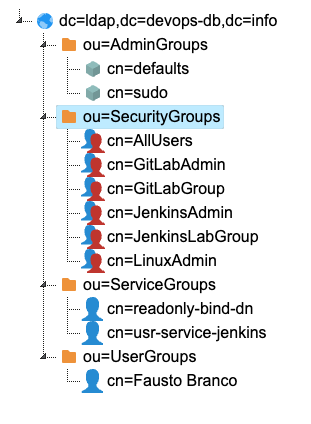
LDAP Structure
Here, there are unusual settings. To make the configurations I made clearer, I first need to show the structure created in LDAP for Jenkins.
For Jenkins, I created 2 groups (memberOf), one for administrative access and another for access that will be used by other services, GitLab, for example.
| Use | LDAP Group |
|---|---|
| services | cn=JenkinsLabGroup,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info |
| administrative | cn=JenkinsAdmin,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info |
At this moment, I have my user, which is a memberOf the JenkinsAdmin group and I created a user usr-service-jenkins which is a memberOf the JenkinsLabGroup group. The LDIF files are all on GitHub.
rm /work/jenkins/JenkinsAdmin_sec_group.ldif
cat << EOL > /work/jenkins/JenkinsAdmin_sec_group.ldif
dn: cn=JenkinsAdmin,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info
objectClass: groupOfNames
member: cn=Fausto Branco,ou=UserGroups,dc=ldap,dc=devops-db,dc=info
EOL
ldapadd -x -H ldaps://ldap.devops-db.info:636 -D "CN=admin,dc=ldap,dc=devops-db,dc=info" -f /work/jenkins/JenkinsAdmin_sec_group.ldif -w "JbBmKx#lK@ZX4*amqd5l"
#######################################################################################################################
rm /work/jenkins/JenkinsLabGroup_sec_group.ldif
cat << EOL > /work/jenkins/JenkinsLabGroup_sec_group.ldif
dn: cn=JenkinsLabGroup,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info
objectClass: groupOfNames
member: cn=Fausto Branco,ou=UserGroups,dc=ldap,dc=devops-db,dc=info
EOL
ldapadd -x -H ldaps://ldap.devops-db.info:636 -D "CN=admin,dc=ldap,dc=devops-db,dc=info" -f /work/jenkins/JenkinsLabGroup_sec_group.ldif -w "JbBmKx#lK@ZX4*amqd5l"
#######################################################################################################################
rm /work/jenkins/teste_user.ldif
cat << EOL > /work/jenkins/teste_user.ldif
## Users
dn: cn=usr-service-jenkins,ou=ServiceGroups,dc=ldap,dc=devops-db,dc=info
gidnumber: 10003
givenname: Service
homedirectory: /home/usrservicejenkins
loginshell: /bin/bash
objectclass: posixAccount
objectclass: inetOrgPerson
objectclass: organizationalPerson
objectclass: person
sn: Jenkins
uid: usr-service-jenkins
uidnumber: 10003
mail: fausto.branco@gmail.com
userpassword: {SSHA}IYJhwtAEaBJM5Epume4A+0fN84iU9eXZ
EOL
ldapadd -x -H ldaps://ldap.devops-db.info:636 -D "cn=admin,dc=ldap,dc=devops-db,dc=info" -f /work/jenkins/teste_user.ldif -w "JbBmKx#lK@ZX4*amqd5l"
#######################################################################################################################
rm /work/jenkins/add_user_to_group.ldif
cat << EOL > /work/jenkins/add_user_to_group.ldif
dn: cn=JenkinsLabGroup,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info
changetype: modify
objectClass: groupOfNames
member: cn=Fausto Branco,ou=UserGroups,dc=ldap,dc=devops-db,dc=info
EOL
ldapadd -x -H ldaps://ldap.devops-db.info:636 -D "CN=admin,dc=ldap,dc=devops-db,dc=info" -f /work/jenkins/add_user_to_group.ldif -w "JbBmKx#lK@ZX4*amqd5l"
Certificate for TLS
Before starting configuration, we also need to copy the certificate so we can use TLS. The certificate I use, I already show in previous posts how to generate and copy what we need.
At this point, I’m going to assume that you know how to copy the certificate and it is in the /etc/ssl/certs/ldapcacert.crt folder.
With sudo access to the VM, we need to copy the certificate to the security folder of your Java Home. Then, using the keytool application and adding the certificate to a keystore/truststore, only then can Java load the certificate and we can use TLS.
cp /etc/ssl/certs/ldapcacert.crt $JAVA_HOME/conf/security
cd $JAVA_HOME/conf/security
keytool -cacerts -storepass changeit -noprompt -trustcacerts -importcert -alias ldapcert -file ldapcacert.crtThen, restart Jenkins service (or container)
Configuration
In security, in the first configuration options there is Security Realm, choose LDAP:

When expanding the “Advanced Server Configuration” item, several options are presented, here I leave a print of how the configuration turned out and a description of some.
| Item | Description |
|---|---|
| root DN | Basic/root DN of your LDAP, typically your LDAP DC. —- dc=ldap,dc=devops-db,dc=info |
| User search base | It is used to identify a root OU for users, for example ou=UserGroups. If all users are within a single OU, it is possible to use this setting, but in my case, they will be in two different OUs, so leave it blank, Jenkins does a hierarchical search. |
| User search filter | This is the filter itself. Here you can restrict the groups, OUs, etc. of users who will be allowed to login. In my case, users must be a memberOf one of two groups: JenkinsAdmin or JenkinsLabGroup. —- (&(uid={0})(|(memberOf=cn=JenkinsAdmin,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info)(memberOf=cn=JenkinsLabGroup,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info))) |
| Group search base | This configuration is used for Jenkins to be able to list groups that exist in LDAP and are associated with the security roles that will be created (in our case). Here the base OU of where the groups are located is configured. —- ou=SecurityGroups |
| Group search filter | Indicate, if necessary, which type of object (groups) will be searched for in the above listing, I chose to use only the groups that are used as memberOf (objectclass=groupOfNames) —- (&(cn={0})(objectclass=groupOfNames)) |
| Group membership attribute | Which user attribute will be used in the comparison with groups / roles. memberOf —- memberOf |
| Manager DN | DN that will be used for searches, we will use the readonly-bind-dn that we created in another post. —- cn=readonly-bind-dn,ou=ServiceGroups,dc=ldap,dc=devops-db,dc=info |
| Display Name LDAP attribute | What attribute will be used for the names of both groups and users. —- cn |
At the end of the configuration, before saving or applying, do the “Test LDAP Settings”, validate if the settings are correct, if the user brings their groups, etc. In the image, the items at the end, with an icon showing, indicate that the test went well.
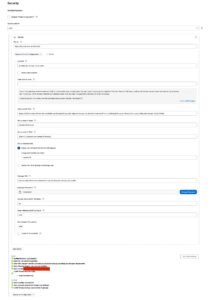
At this point, you already have Jenkins authenticating with LDAP, initially, if there are no Roles configurations, users will be authenticated as admin.
In the next post, I show how to configure the Role management plugin with LDAP.
Leave a Reply