Settings
There isn’t much of a secret to configuring GitLab to use LDAP integration, but it doesn’t have a graphical mode, we have to change directly in the configuration files and then reconfigure it.
More information on the GitLab page: Integrate LDAP with GitLab | GitLab
Before starting, it’s worth doing a connectivity test between the GitLab VM and LDAP:
$ ldapwhoami -vvv -H 'ldap://ldap.devops-db.info:389' -D 'cn=Fausto Branco,ou=UserGroups,dc=ldap,dc=devops-db,dc=info' -x -W
ldap_initialize( ldap://ldap.devops-db.info:389/??base )
Enter LDAP Password:
dn:cn=Fausto Branco,ou=UserGroups,dc=ldap,dc=devops-db,dc=info
Result: Success (0)Certificate preparation.
First, you need to copy the OpenLDAP certificate to the Gitlab host. The certificate is in /etc/ssl/openldap/certs/ldapserver-cert.crt, we can do this in several ways, I’ll leave two of the simplest.
Please note that the content will vary depending on the certificates you created, these are examples that were created by me.
From within the OpenLDAP host, cat the file and take the content between BEGIN CERTIFICATE and END CERTIFICATE
cat /etc/ssl/openldap/certs/ldapserver-cert.crt
[...]
-----BEGIN CERTIFICATE-----
MIIFwjCCA6qgAwIBAgICEAEwDQYJKoZIhvcNAQELBQAwgYQxCzAJBgNVBAYTAlBU
MQ4wDAYDVQQIDAVQb3J0bzEOMAwGA1UEBwwFUG9ydG8xEjAQBgNVBAoMCURldm9w
cy1EQjEcMBoGA1UEAwwTbGRhcC5kZXZvcHMtZGIuaW5mbzEjMCEGCSqGSIb3DQEJ
ARYUYWRtaW5AZGV2b3BzLWRiLmluZm8wHhcNMjQwNDA4MTEzMzE0WhcNMjUwNDA4
MTEzMzE0WjB0MQswCQYDVQQGEwJQVDEOMAwGA1UECAwFUG9ydG8xEjAQBgNVBAoM
CURldm9wcy1EQjEcMBoGA1UEAwwTbGRhcC5kZXZvcHMtZGIuaW5mbzEjMCEGCSqG
SIb3DQEJARYUYWRtaW5AZGV2b3BzLWRiLmluZm8wggIiMA0GCSqGSIb3DQEBAQUA
A4ICDwAwggIKAoICAQCz6rcxPNUdN37jfFmMf/Mwdxmf6ST3hulCJAxNBBHzOSOW
+umvVhfqtw88X3dgq3CW7fQvGQ2izqzN/2MLSe7yV9I1LGqLmtwN2IHTTpC3NAeH
8qlfuwHi+IvO2eFr0EGaL4rT5O+h8qnthPWI1/Rh9xdkx9xvTvVTsElkNZJ+zAZs
E41XwWRsxwHUyDRxQIL2EGbUVyjbJgTzoxQQHdetIeYc6Vya7ABHa6iwfSMKR99A
NdOujpnNecGnGJSzQ0B6RXp2ae28LjjyVdMV1wo6PrvgsKqt5MO4GxyPKginVp0s
ly2zVshCzREw6/4lxxJXqRHcmcS6mhm0U77QTG32A2bU+SJONqxF6GVil60sGm59
MxwDvkgQuE9QDQ4+txYh8K97PfxqVcPG92PS2sYOinc1EBsnD6TEsuvfc8m0Ev3m
njZ+jgJA4Gf+e9AbfgQVJEbdQj7mM2gRFL7CWKAgzk2KRh9xWTlk8nCwqCwHx57d
hE+qfC/SkInZCQHGTSQ22+RidEXq7GxtY2KDNSFSTPeGjR8KA5+lqeuIf8ZeHc6s
HEtK12B8yvYDfRyCBnPugXxs77CiTcmUvWCfBP9GZv4icoCdDTzfnfTNaGO9X16+
XY5sC27o24WsxXLF9EDtp6FpnGX1moR6h89Jky+clCwpDUj4sucWz4WPtHpAnwID
AQABo00wSzAJBgNVHRMEAjAAMB0GA1UdDgQWBBTP5qF7BCcepDXMDBBq+Bbonlr2
FzAfBgNVHSMEGDAWgBRN6D0ZxNB2qFyd9JTxZ/oYSBfMTjANBgkqhkiG9w0BAQsF
AAOCAgEAjz2Hx2s8A+liNwaEGPS1B/TDHDUKgzsrjXPEVfni3vhlhqgczej/rDAX
d8pLJ4QawlFPbQVZqFFsyJjo6dAG2WfIJeA0c+7kw1pVcbVqQKymq7UtOaHiZF8j
jkBuxKJH4P+lxBLSWCiktvqhTJ/1IgQ66R3wve8J0+KCHGsX2BFMA8Zqc48PTXnu
NGLUsIIYNwMlsCyfEYRY9s6Lg5q8Vcb1dN39uJwMe+Q8XKM0tPM+Dn1z4289q9CZ
poGfhonu3u/9e/LsrptE0ZURGqBFCXXU8gAq0Yg1ViGwcA8e6HC6iia6H0Y4vS6j
q33VIswn0In56zw4gOD/BnYHU5B/277hY8UIsU6vQaTZbpE/GpW8RT85V4MT6r5W
MI2WF8ZATyBbJ5PbXctYfmnydQwTXpoNnioGmxH4Qu0S+ydc+yneAIlZWURlq5gB
YuZrmI7xuGxs5UfzQBEFroRlI6QmW95ebkac5XwURTW1/bI5deJZnfTOezRJKr5n
L1yySSIs2rYXQkphDwV6HqSNg3eJSEGusCbV9Kgx52X5uorfot5i1bZUJcSKJJby
38UpFzQ4/SOBewNfWAq6Q1NBWUbfn8BARv96L7n3uK4JrxfkUrHGjzWGJmtlgx+b
shJhA/b/35i7KxmdI6eGy0I3vylbGjaH0WGS4+QRYeJKWXPm6kk=
-----END CERTIFICATE-----Run the command below from any host and also, take the content between BEGIN CERTIFICATE and END CERTIFICATE
openssl s_client -connect ldap.devops-db.info:389 -starttls ldap -showcerts < /dev/null | openssl x509 -text | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p'
[...]
-----BEGIN CERTIFICATE-----
MIIFwjCCA6qgAwIBAgICEAEwDQYJKoZIhvcNAQELBQAwgYQxCzAJBgNVBAYTAlBU
MQ4wDAYDVQQIDAVQb3J0bzEOMAwGA1UEBwwFUG9ydG8xEjAQBgNVBAoMCURldm9w
cy1EQjEcMBoGA1UEAwwTbGRhcC5kZXZvcHMtZGIuaW5mbzEjMCEGCSqGSIb3DQEJ
ARYUYWRtaW5AZGV2b3BzLWRiLmluZm8wHhcNMjQwNDA4MTEzMzE0WhcNMjUwNDA4
MTEzMzE0WjB0MQswCQYDVQQGEwJQVDEOMAwGA1UECAwFUG9ydG8xEjAQBgNVBAoM
CURldm9wcy1EQjEcMBoGA1UEAwwTbGRhcC5kZXZvcHMtZGIuaW5mbzEjMCEGCSqG
SIb3DQEJARYUYWRtaW5AZGV2b3BzLWRiLmluZm8wggIiMA0GCSqGSIb3DQEBAQUA
A4ICDwAwggIKAoICAQCz6rcxPNUdN37jfFmMf/Mwdxmf6ST3hulCJAxNBBHzOSOW
+umvVhfqtw88X3dgq3CW7fQvGQ2izqzN/2MLSe7yV9I1LGqLmtwN2IHTTpC3NAeH
8qlfuwHi+IvO2eFr0EGaL4rT5O+h8qnthPWI1/Rh9xdkx9xvTvVTsElkNZJ+zAZs
E41XwWRsxwHUyDRxQIL2EGbUVyjbJgTzoxQQHdetIeYc6Vya7ABHa6iwfSMKR99A
NdOujpnNecGnGJSzQ0B6RXp2ae28LjjyVdMV1wo6PrvgsKqt5MO4GxyPKginVp0s
ly2zVshCzREw6/4lxxJXqRHcmcS6mhm0U77QTG32A2bU+SJONqxF6GVil60sGm59
MxwDvkgQuE9QDQ4+txYh8K97PfxqVcPG92PS2sYOinc1EBsnD6TEsuvfc8m0Ev3m
njZ+jgJA4Gf+e9AbfgQVJEbdQj7mM2gRFL7CWKAgzk2KRh9xWTlk8nCwqCwHx57d
hE+qfC/SkInZCQHGTSQ22+RidEXq7GxtY2KDNSFSTPeGjR8KA5+lqeuIf8ZeHc6s
HEtK12B8yvYDfRyCBnPugXxs77CiTcmUvWCfBP9GZv4icoCdDTzfnfTNaGO9X16+
XY5sC27o24WsxXLF9EDtp6FpnGX1moR6h89Jky+clCwpDUj4sucWz4WPtHpAnwID
AQABo00wSzAJBgNVHRMEAjAAMB0GA1UdDgQWBBTP5qF7BCcepDXMDBBq+Bbonlr2
FzAfBgNVHSMEGDAWgBRN6D0ZxNB2qFyd9JTxZ/oYSBfMTjANBgkqhkiG9w0BAQsF
AAOCAgEAjz2Hx2s8A+liNwaEGPS1B/TDHDUKgzsrjXPEVfni3vhlhqgczej/rDAX
d8pLJ4QawlFPbQVZqFFsyJjo6dAG2WfIJeA0c+7kw1pVcbVqQKymq7UtOaHiZF8j
jkBuxKJH4P+lxBLSWCiktvqhTJ/1IgQ66R3wve8J0+KCHGsX2BFMA8Zqc48PTXnu
NGLUsIIYNwMlsCyfEYRY9s6Lg5q8Vcb1dN39uJwMe+Q8XKM0tPM+Dn1z4289q9CZ
poGfhonu3u/9e/LsrptE0ZURGqBFCXXU8gAq0Yg1ViGwcA8e6HC6iia6H0Y4vS6j
q33VIswn0In56zw4gOD/BnYHU5B/277hY8UIsU6vQaTZbpE/GpW8RT85V4MT6r5W
MI2WF8ZATyBbJ5PbXctYfmnydQwTXpoNnioGmxH4Qu0S+ydc+yneAIlZWURlq5gB
YuZrmI7xuGxs5UfzQBEFroRlI6QmW95ebkac5XwURTW1/bI5deJZnfTOezRJKr5n
L1yySSIs2rYXQkphDwV6HqSNg3eJSEGusCbV9Kgx52X5uorfot5i1bZUJcSKJJby
38UpFzQ4/SOBewNfWAq6Q1NBWUbfn8BARv96L7n3uK4JrxfkUrHGjzWGJmtlgx+b
shJhA/b/35i7KxmdI6eGy0I3vylbGjaH0WGS4+QRYeJKWXPm6kk=
-----END CERTIFICATE-----
With the content obtained, in any of the ways above and back on the Gitlab host, create the file: /etc/ssl/certs/ldapcacert.crt
I already have this certificate saved on my Host, so I can distribute it among the other hosts I created.
Later, it will also be added to this GitLab, so automations will be able to be copied to any other.
Validate the certificate by connecting to the LDAP host
$ openssl s_client -connect ldap.devops-db.info:389 -CAfile /etc/ssl/certs/ldapcacert.crt
CONNECTED(00000003)
40C75159867F0000:error:0A000126:SSL routines:ssl3_read_n:unexpected eof while reading:../ssl/record/rec_layer_s3.c:308:
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 0 bytes and written 321 bytes
Verification: OK
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---Change the LDAP configuration file to add the certificate we created above.
vi /etc/ldap/ldap.conf
TLS_CACERT /etc/ssl/certs/ldapcacert.crtRun the tests, with and without TLS.
ldapwhoami -vvv -H 'ldap://ldap.devops-db.info:389' -D 'cn=Fausto Branco,ou=UserGroups,dc=ldap,dc=devops-db,dc=info' -x -W
ldapwhoami -vvv -H 'ldaps://ldap.devops-db.info:636' -D 'cn=Fausto Branco,ou=UserGroups,dc=ldap,dc=devops-db,dc=info' -x -W
GitLab configuration.
In the bash of the VM where Gitlab is installed, we need to edit the /etc/gitlab/gitlab.rb file and add the complete configuration section below:
Never replace the file completely, this is just a configuration section. If you do, you can break your GitLab installation.
gitlab_rails['ldap_enabled'] = true
gitlab_rails['ldap_servers'] = {
'main' => {
'label' => 'Devops-db',
'host' => 'ldap.devops-db.info',
'port' => 636,
'uid' => 'uid',
'bind_dn' => 'cn=admin,dc=ldap,dc=devops-db,dc=info',
'password' => 'JbBmKx#lK@ZX4*amqd5l',
'encryption' => 'simple_tls',
'verify_certificates' => false,
'active_directory' => false,
'lowercase_usernames' => 'false',
'retry_empty_result_with_codes' => [80],
'allow_username_or_email_login' => false,
'base' => 'dc=ldap,dc=devops-db,dc=info',
'tls_options' => {
'ca_file' => '/etc/ssl/certs/ldapcacert.crt',
'ssl_version' => 'TLSv1_2'
},
'user_filter' => '(&(objectClass=person)(memberOf=cn=GitLabGroup,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info))'
}
}
The settings above are for the LDAP created and configured for the purpose of this lab.
The ‘user_filter’ parameter is optional, without it, GitLab/Ldap will only validate if the user is in the ‘base’ query and if the password is OK. With this, everyone can access GitLab
To restrict access a little, I put the filter “cn=GitLabGroup,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info“, so only users who are in the GitLabGroup group can use GitLab.
It is possible to concatenate groups, for example:
'user_filter' => '(&(objectClass=user)(|(memberOf=cn=GitLabGroup,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info)(memberOf=cn=DevOpsLabGroup,ou=SecurityGroups,dc=ldap,dc=devops-db,dc=info)))'But anyway, run the command to reconfigure GitLab
gitlab-ctl reconfigureGitlab may take a few minutes to return.
Validate the configuration:
$ gitlab-rake gitlab:ldap:check
Checking LDAP ...
LDAP: ... Server: ldapmain
not verifying SSL hostname of LDAPS server 'ldap.devops-db.info:636'
LDAP authentication... Success
LDAP users with access to your GitLab server (only showing the first 100 results)
DN: cn=fausto branco,ou=usergroups,dc=ldap,dc=devops-db,dc=info uid: fbranco
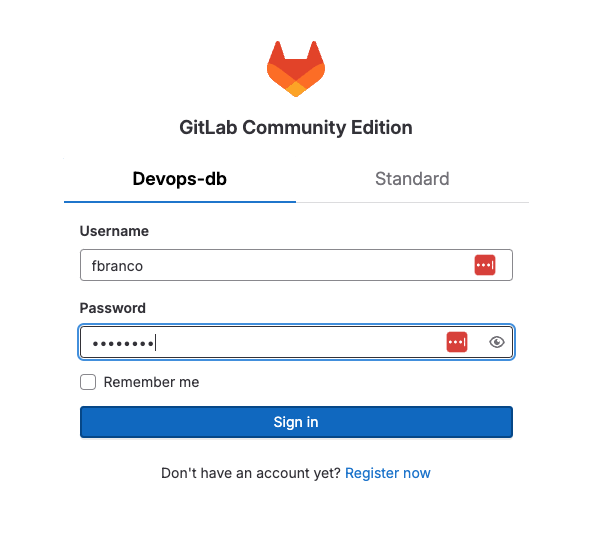
Checking LDAP ... FinishedNew Login
Note that now the login screen has changed, there is the option to log in with AD, the Label is the one configured in the file above.
Leave a Reply